As announced on December 14, when Alias Robotics confirmed it's entry in Telefónica Tech's investment portfolio, both companies are leading the creation of the first 5G robotics cybersecurity lab worlwide, to be located at Wayra's facilities in Munich. Now, we want to take a closer look at what the CS4R (CyberSecurity For Robotics) lab will be and all the ins and outs of its creation.
The CS4R lab will be placed at Wayra's facilities in Munich. It will also be used as a demo room for RIS (Robot Immune System) and the rest of Alias Robotics' robot cybersecurity portfolio. It will mimic a robotic chain where clients and partners will have the chance to experience and test different robotic platforms, getting an insight of our company's threat intelligence and protection capabilities.
The initial demonstration consists on 3 different robotic platforms, being representative of most used robots. An industrial robotic platform, a collaborative robot, and an AMR (Autonomous Mobile Robot) will be synchronized in a simulated application. "This way we can show how an attacker can break the synchronization by attacking one of the robots and how RIS defends the endpoint once installed" explains Alfonso, our offensive security technician.
Connectivity and synchronization between different robotic platforms is a highly complex task. Different robots and associated components require different connection paradigms, and it is always a technical challenge to interconnect different platforms across such disparate systems.
Each robotic platform has specific vulnerabilities, meaning that threat intelligence needs to be gathered for each platform. An array of cyberattacks will be displayed at the different robotic paltforms at the CS4R lab.
A remotely triggered denial of service will be showcased as the initial demonstration for the industrial robot. This means the robot's activity can be interrupted by an external bad actor causing major economic cost and operative risk for industrial players.
For the AMR the first attack will be a remote task termination, unexpectedly triggering a halt. This attack in production could be dangerous, e.g if it stops blocking the way of an evacuation area. The second attack will activate a service inside the AMR, in our scenario a sound. The same procedure can be used to activate UV lamp equipped AMRs, which have been used in hospitals due to the COVID-19 pandemic for stirilization.
Finally, the collaborative robot will suffer a remotely denial of service, a ransomware, and a malicious file deployment via USB. "This is the nightmare of any company, as in any of the 3 attacks the loss by stopping the line is substantial. The most common and damming attack is ramsoware, a hijack of the controller until the user pays to get the control back" claims Alfonso.
In order to achieve the reproducibility of the setup, a virtual lab has been created using Gazebo. This virtual laboratory will be a carbon copy of the one in Munich, and the simulated robots will behave exactly as the real ones. Future attendees to this virtual lab will be able to experiment with our robot cybersecurity portfolio in action remotely.
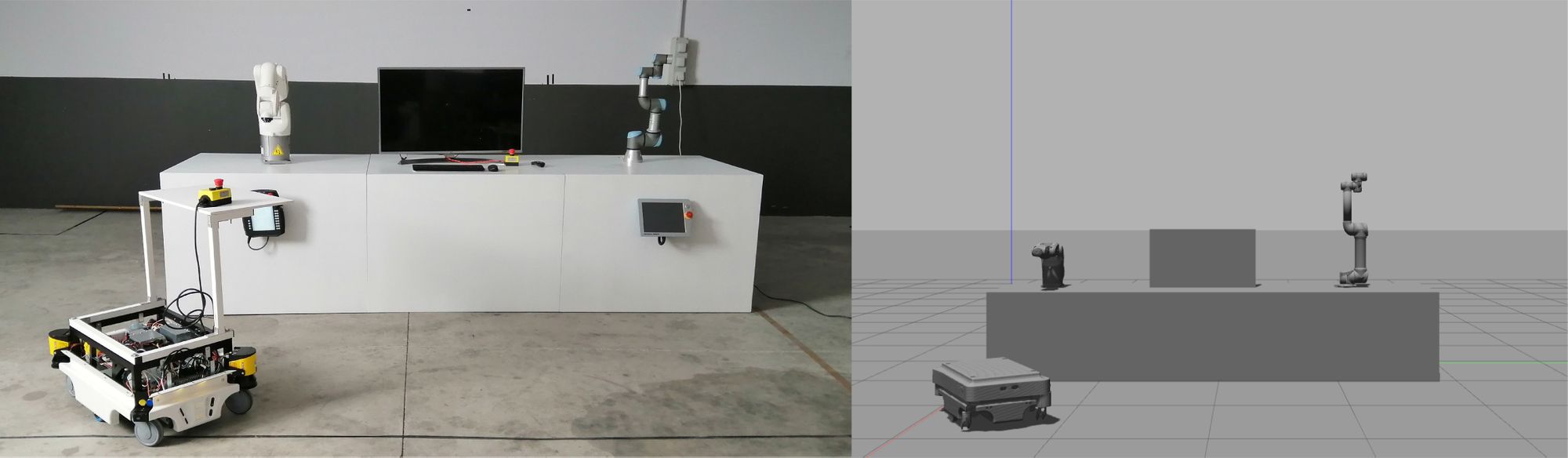
Before CS4R lands at Wayra, RIS has been tested in Telefonica central headquarters in Madrid. During the demonstration, some of the attacks were launched by Alias' team members and stopped by the endpoint protection platform, RIS.

Next steps of CS4R will be in Munich, stay tuned and get informed on our social media.


