Alias Robotics discovers numerous and dangerous vulnerabilities in the Robot Operating System’s (ROS) communications that can have “devastating consequences”
Alias Robotics discover about 15 dangerous vulnerabilities affecting DDS, the default communications middleware of ROS 2 and propose tools to detect them.

| Press release (English) | link |
| Press release (Spanish) | link |
| SROS2: Usable Cyber Security Tools for ROS 2 paper | link |
- The robot cyber security firm from Vitoria-Gasteiz (Spain) is once again leading an investigation involving international experts on the importance of security in the Robot Operating System (ROS) and the DDS communications middleware
- The participants in the study have discovered more than a dozen of dangerous vulnerabilities present in more than 650 devices online today, very common in the industrial field, the University, and even in Hospitals and Military Agencies
- Alias Robotics' research has been cited and published by the United States Cybersecurity Infrastructure and Security Agency, which reflects the importance of the conclusions set forth.
- To mitigate these vulnerabilities, Alias Robotics has contributed to SROS2, a series of developer tools to detect insecurities in ROS 2 and DDS
A team of researchers led by the Spanish firm Alias Robotics - specialized in robotic cybersecurity - together with cybersecurity experts from several multinationals and cybersecurity professionals from various governments, have discovered about fifteen dangerous vulnerabilities, some critical, in the Robot Operating System (ROS) and the DDS communications protocols that affect industrial systems and robots that, if used by cybercriminals, could have "devastating consequences. In turn, they have detected that these vulnerabilities are present in almost 650 different devices exposed on the Internet and used not only in industry, but also in healthcare or in the military field.
Robotics and IT security professionals from the firm Alias Robotics in Spain have collaborated in recent months with security experts from around the world in the detection of security vulnerabilities in the Robot Operating System (ROS) and in the software communications middleware DDS (“Data Distribution Service”), present in many systems (autonomous cars, industrial robotic arms, aerospace systems, military equipment, critical infrastructure, …), as well as in industrial robots.
In particular, the vulnerabilities affect DDS, an 'intermediate software' (called middleware) that is the main communication bus between different robotic devices, that is, the core of ROS 2 (Robot Operating System ), which is used by the majority of robotics engineers for all types of present or future industrial robots, with applications in the business world, in the industrial field, but also in the world of health, as is the case of surgical robots. An independent study[1] suggests that the use of ROS will grow significantly over the next few years and that by 2024, 55% of commercialized robots will use ROS.
From Alias Robotics -specialized in robot cyber security- it is considered that “DDS is a middleware still largely insecure communications technology, used in areas where security is very important, so investment in cybersecurity is needed immediately”. They also consider that the response times of the DDS manufacturers are too long, "which greatly exposes these systems to cyber-attacks," according to Víctor Mayoral-Vilches, a leading robot cybersecurity researcher from Alias Robotics and founder of the startup.
In his opinion, “cybercriminals could today use these vulnerabilities to paralyze robots and critical infrastructures all over the world leveraging DDS”. The company from Vitoria warns that it is necessary for robotics and automation companies to invest in cybersecurity and cooperate "with qualified groups in robot cybersecurity".
Summary of results
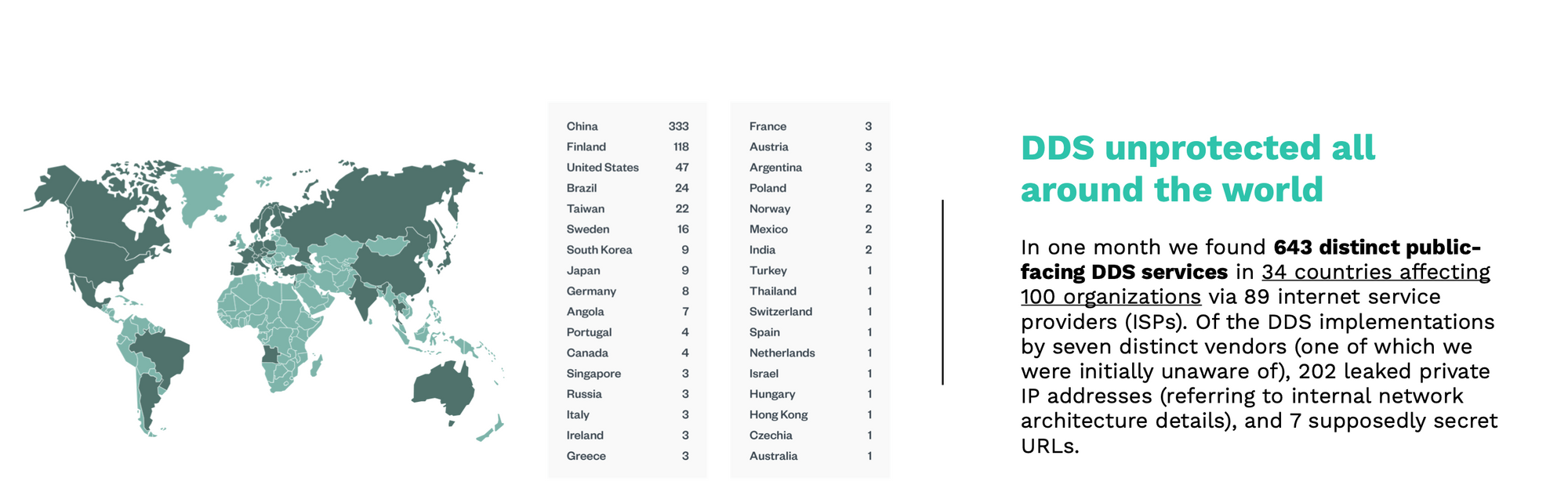
The results of this research derive from the collaboration of several researchers including Víctor Mayoral-Vilches (Alias Robotics), Federico Maggi, Mars Cheng, Patrick Kuo, Chizuru Toyama, Rainer Vosseler, and Ta-Lun Yen (Trend Micro and TxOne) and Erik Boasson (ADLINK Labs).
Its impact in robotics has been led by Alias Robotics and a good part of these vulnerabilities “have not been patched or mitigated by the manufacturers serving robotics companies today".
The team of researchers has come to detect up to 13 security vulnerabilities (some classified as "critical" by cybersecurity experts), which could affect both workers and users who handle industrial robots that include this DDS software. Based on the security-immaturity of DDS, the appearance of new vulnerabilities affecting DDS in the coming months is not ruled out.
One of the conclusions is that these vulnerabilities are present in almost 650 different devices used in across areas of application around the world. From Alias Robotics they have detected devices affected by these vulnerabilities in organizations such as NASA, but also in global data centers (Huawei Cloud Service), large industrial multinationals (Siemens), as well as hospitals, banks and universities in 34 countries, affecting 100 organizations through 89 Internet Service Providers (ISPs).
Key vulnerability findings
These detected vulnerabilities could lead to the loss of control of the robotic device, its complete loss of security, the denial of services through brute force, the possibility of facilitating access to the device through the exploitation of remote services, problems in the supply chain or the fact that attackers abuse the security protocols themselves to create an efficient command and control channel.
The authors of the study, have found that many of these security vulnerabilities - some even with the source code (proprietary) exposed to the public - have been open "for a long time, even years, so today cybercriminals could use them to paralyze critical infrastructure around the world” , according to Víctor Mayoral-Vilches.
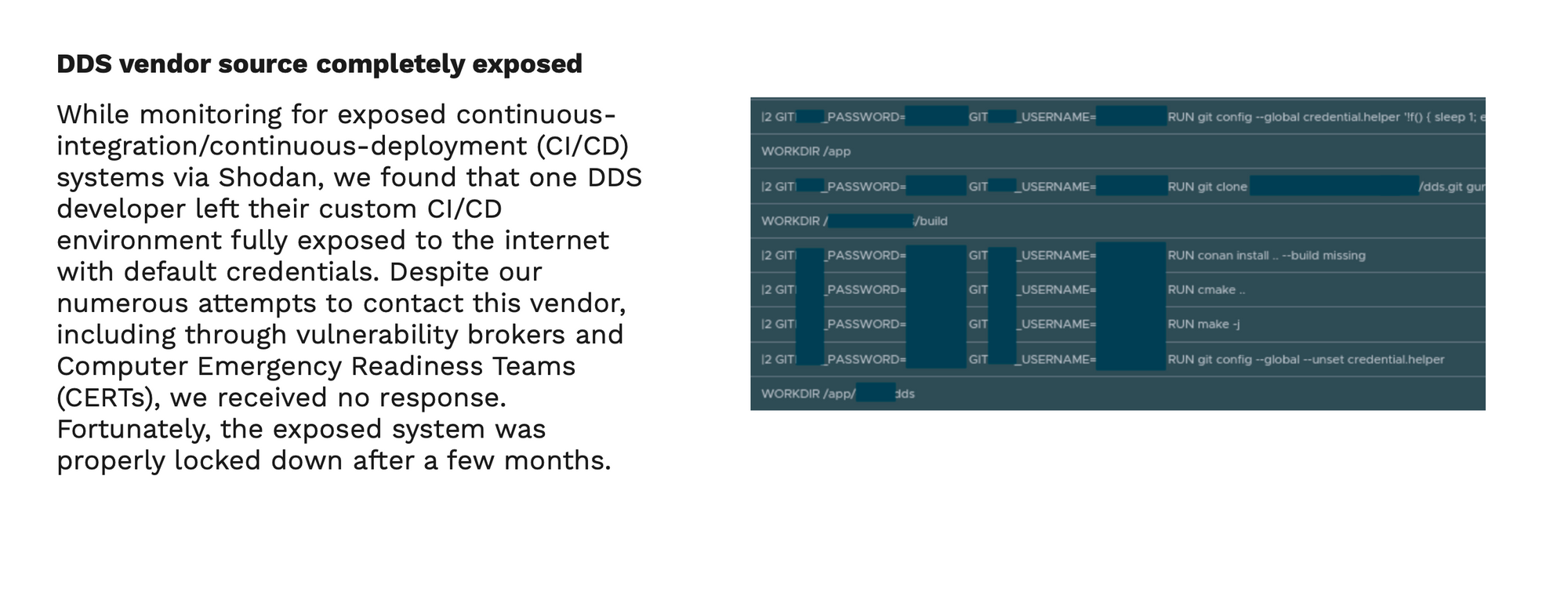
In his opinion, “many still robotic device manufacturers prioritize their business development and continue to ignore cybersecurity.” Mayoral-Vilches emphasizes that many of the manufacturers refuse to solve the problems “because if they did they would not comply with the DDS standard/specification”. This is a problem of magnitude” - emphasizes the founder of Alias Robotics - “since the revision of the DDS standard may take years to be properly revised“.
The report, which has been recently cited and published by the United States Agency for Security and Cybersecurity Infrastructure, was presented during 2021 in various forums including 'Black Hat 2021' from Las Vegas, the world's largest annual cybersecurity forum - but also at the ROS-Industrial Conference 2021 and more recently at a session organized by the European Commission on safety, security and performance. His research will continue to be presented throughout 2022 at new conferences and industry forums.
Tools to identify ROS 2 and DDS vulnerabilities
In order to mitigate the threats found and train robotics engineers in security matters, the Alias Robotics team has led a second research effort that has contributed and released a series of extensions to tools under an open source license that allow detecting these vulnerabilities in ROS 2 and DDS.
The results of this effort have been summarized in the article "SROS2: Usable Cyber Security Tools for ROS 2" which has been sent to the International Conference on Robots and Systems (IROS 2022).
About Alias Robotics
Founded in 2018 by Víctor Mayoral-Vilches, Alias Robotics is an international leader in robotic cybersecurity solutions including its robot cybersecurity services, as well as its Robot Immune System (RIS), a cybersecurity product that’s incorporated into robots to protect them against cyber-attacks from the inside, as it evolves and adapts like the human immune system.
Born in Europe and headquarted in Vitoria-Gasteiz (Euskadi, Spain), the team behind Alias is made up of renowned robotics engineers, scientists and security researchers. Its customers include large automation companies, government institutions and large industrial robot users.
The Rise of ROS: Nearly 55% of total commercial robots shipped in 2024 Will Have at Least One Robot Operating System package Installed, https://www.businesswire.com/news/home/20190516005135/en/Rise-ROS-55-total-commercial-robots-shipped ↩︎


