We propose a cybersecurity methodology to secure computational graphs and improve SROS2, usable security tools for ROS 2. We argue that without usability, security in robotics will be greatly impaired.
First published in ROS Discourse. Read our paper for more: SROS2, Usable Cyber Security tools for ROS 2.
Cyber security is a two-way street where both vendors and researchers must act responsibly and over the last few years we learned that doing security research and cooperating with authorities for responsible disclosure is as important as taking appropriate measures and mitigations in a timely manner. But for that to happen, [u]security needs to be usable in robotics[/u]. Specially from a user (roboticists' standpoint).
Based on past implementations, and from the experiences of both crafting security tools and using them with customer engagements over a few years now, together with @ruffsl, @gianlucacaiazza and @marguedas, I'm happy to share about our latest piece that focuses precisely on the usability problem described above by contributing with extensions to tools and writing formally about a methodology to secure ROS 2 computational graphs: (paper) SROS2, Usable Cyber Security tools for ROS 2.
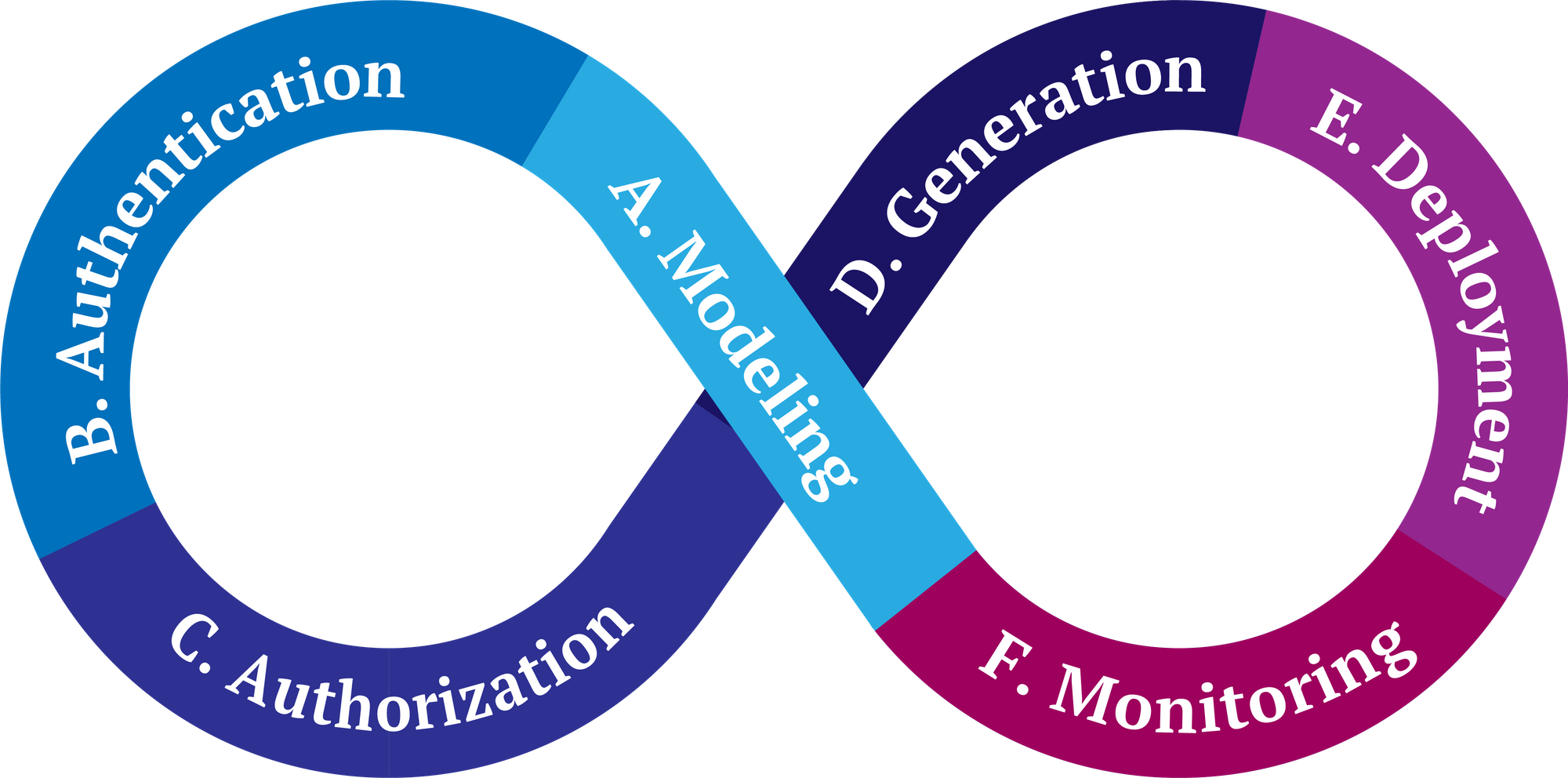
Shortly, our article introduces SROS2 as a series of developer tools, meant to be usable and that facilitate adding security capabilities to ROS 2 computational graphs. We present a security methodology consisting of six steps (heavily inspired by prior DevSecOps work) that allow securing ROS 2 graphs iteratively (and continuously), with the aid of SROS2. Driven by an application use case, we discuss how SROS2 allows achieving security in complex graphs involving popular ROS 2 packages and analyze the security trade-offs and limitations of our current tooling. The key contributions of our work are:
- Introduce SROS2, a set of usable tools for adding security to ROS 2 that: (1) help introspect the computational graph by extracting communication middleware-level information; (2) simplify the security operations creating Identity and Permissions Certificate Authorities (CA) that govern the security policies of a ROS 2 graph; (3) help organize all security artifacts in a consistent manner and within a directory tree that is generated within the current ROS 2 workspace overlay; (4) help create a new identity for each enclave, generating a keypair and signing its x.509 certificate using the appropriate CA; (5) create governance files to encrypt all DDS traffic by default; (6) support specifying enclave permissions in familiar ROS 2 terms which are then automatically converted into low-level DDS permissions; (7) support automatic discovery of required permissions from a running ROS 2 system; and (8) dissect communication middleware interactions, to extract key information for the security monitoring of the system.
- Propose a methodology for securing ROS 2 computational graphs that provides roboticists with a structured process to continuously assess their security.
- Expose insights into how to apply SROS2 to real ROS 2 computational graphs by presenting an application case study focused on analyzing the Navigation2 and SLAM Toolbox stacks in a TurtleBot3 robot.
Besides these, we also acknowledge that SROS2 has various limitations that deserve further attention and improvements (which are fantastic entry points for new contributors!). Some of these include the lack of granularity of security configurations in the current abstractions, which makes it difficult to configure encryption and authentication options separately. Others refer to the lifecycle management of security artifacts, including updating certificates and keys, wherein secure deployment plays a key role. Forward looking, we are particularly keen on improving SROS2 mechanisms in the future to ensure secure lifecycles while minimizing the downtime impact in ROS 2 graphs.
Future work
Some additional promising directions for future work (which hopefully we'll tackle as part of the Security WG) include the development of more advanced monitoring and introspection capabilities, the extension of SROS2 to other communication middlewares (beyond DDS) and finally, the continuous improvement of the usability of the tools. For this, we believe that the use of Graphical User Interfaces (GUIs) represents an interesting opportunity to further facilitate SROS2 usability to non-roboticists.
By releasing this, we're hoping to trigger up the interest of the community in security and inspire groups in robotics to pay more attention to the security to their robotic computational graphs. More exciting work along these lines is in the pipeline, and Alias Robotics has been publishing part of its robot cybersecurity research for a while now, so reach out if you wish to cooperate or just join us in the ROS 2 Security Working Group!

