Securing robot endpoints in Operational Technology (OT) environments
Robots have their own networks, technologies, safety requirements and business priorities, all of which must be addditionally uniquely addressed to secure robots effectively. We extend KICS with RIS to protect robots and prevent safety hazards.

Current Operational Technology (OT) environments protected often include robotic endpoints. Robots have their own networks, technologies, safety requirements and business priorities, all of which must be addditionally uniquely addressed to secure robots effectively. Through a cooperation between Alias Robotics and Kaspersky, we launched a research effort to shed some light on the status of security for robot endpoints in OT environments. Our research showed evidence that simple attacks were feasible and that specialized security controls are necessary for capturing the complexity of modern robot interactions and preventing safety hazards. Read the complete case study here.
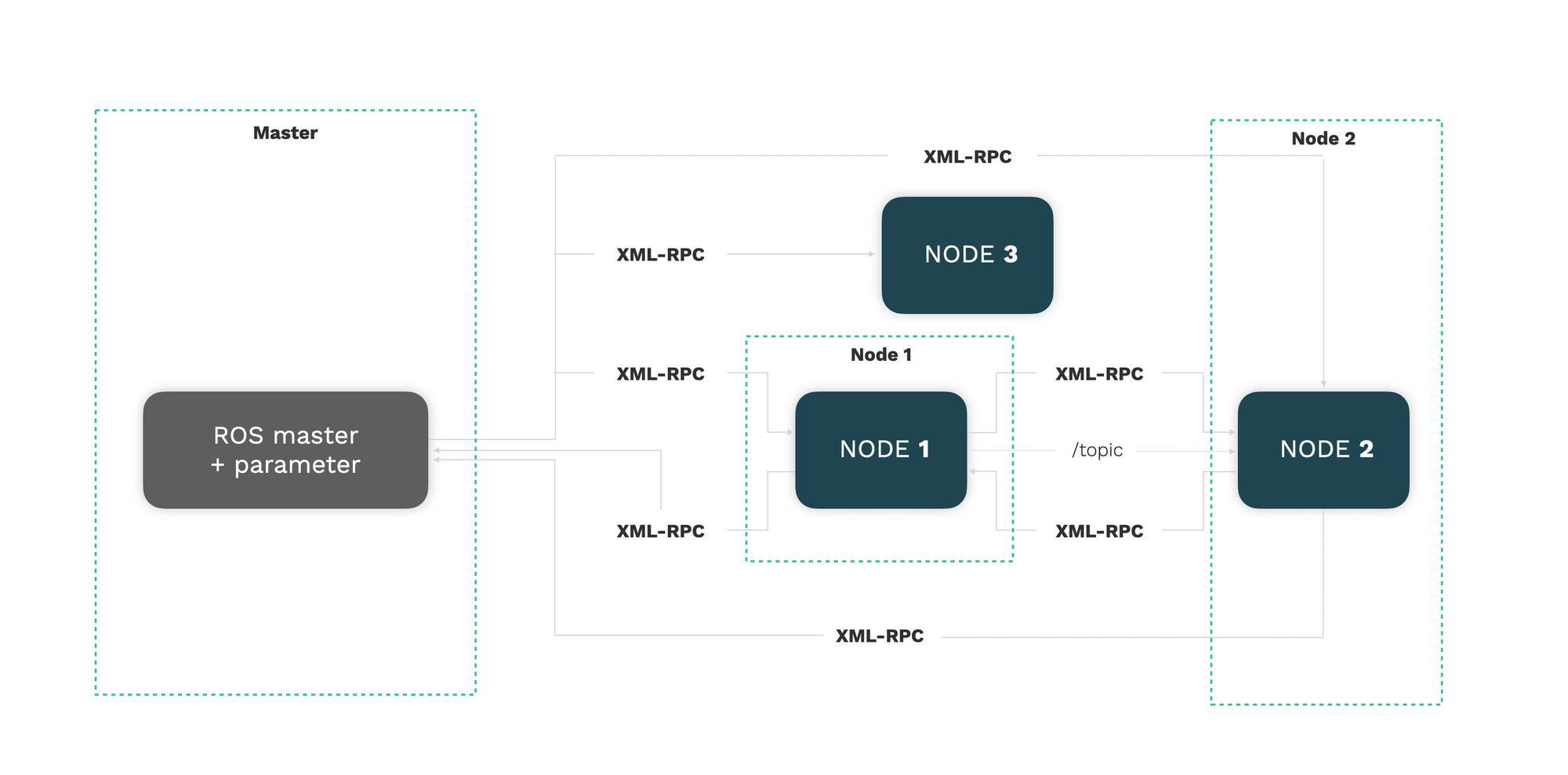
Robot cybersecurity reviews ([1], [2]) criticize the current status of cybersecurity in robotics and reckon the need of further investing in securing these technologies. Previous attempts to review the security of robots via offensive exercises or tools (including [3], [4], [5], [6], [7], [8]) which mostly focus on proof-of-concept attacks and penetration testing, detecting flaws in the Robot Operating System (ROS) [9]. A recent study [10] mentions the identification of several flaws within the ROS-Industrial codebase however it does not explicitly describe exploitable ROS-specific flaws. Considerations are made with regard to the open and insecure architecture predominant in ROS-Industrial deployments throughout its open source drivers. From interactions with the authors of [10:1] it was confirmed that the reported security issues were made generic on purpose, further highlighting the need for further investment on understanding the security landscape of ROS-Industrial setups.
More recent research [11] showed that while ROS is rapidly becoming a standard in robotics (including its growing use in industry), the commonly held assumption that robots are to be deployed in closed and isolated networks does not hold any further and while developments in ROS 2 show promise, the slow adoption cycles in industry will push widespread ROS 2 industrial adoption years from now. Authors at [11:1] claim that ROS will prevail in the meantime and they wonder whether ROS be used securely for industrial use cases even though its origins did not consider it. [8:1] Analyzes this question experimentally by performing a targeted offensive security exercise in a synthetic industrial use case involving ROS-Industrial and ROS packages. The scenario is configured following common OT and ICS practices (including segmentation, segregation and an overall hardening). The authors of [11:2] select one of the most common industrial robots with ROS-Industrial support and configure an industrial environment applying security measures and recommendations. The exercise results in 4 groups of attacks which all manage to compromise the ROS computational graph and all except one take control of most robotic endpoints as desired.
In order to analyze the security of the robotic endpoints Alias Robotics has considered 3 different attack vectors.
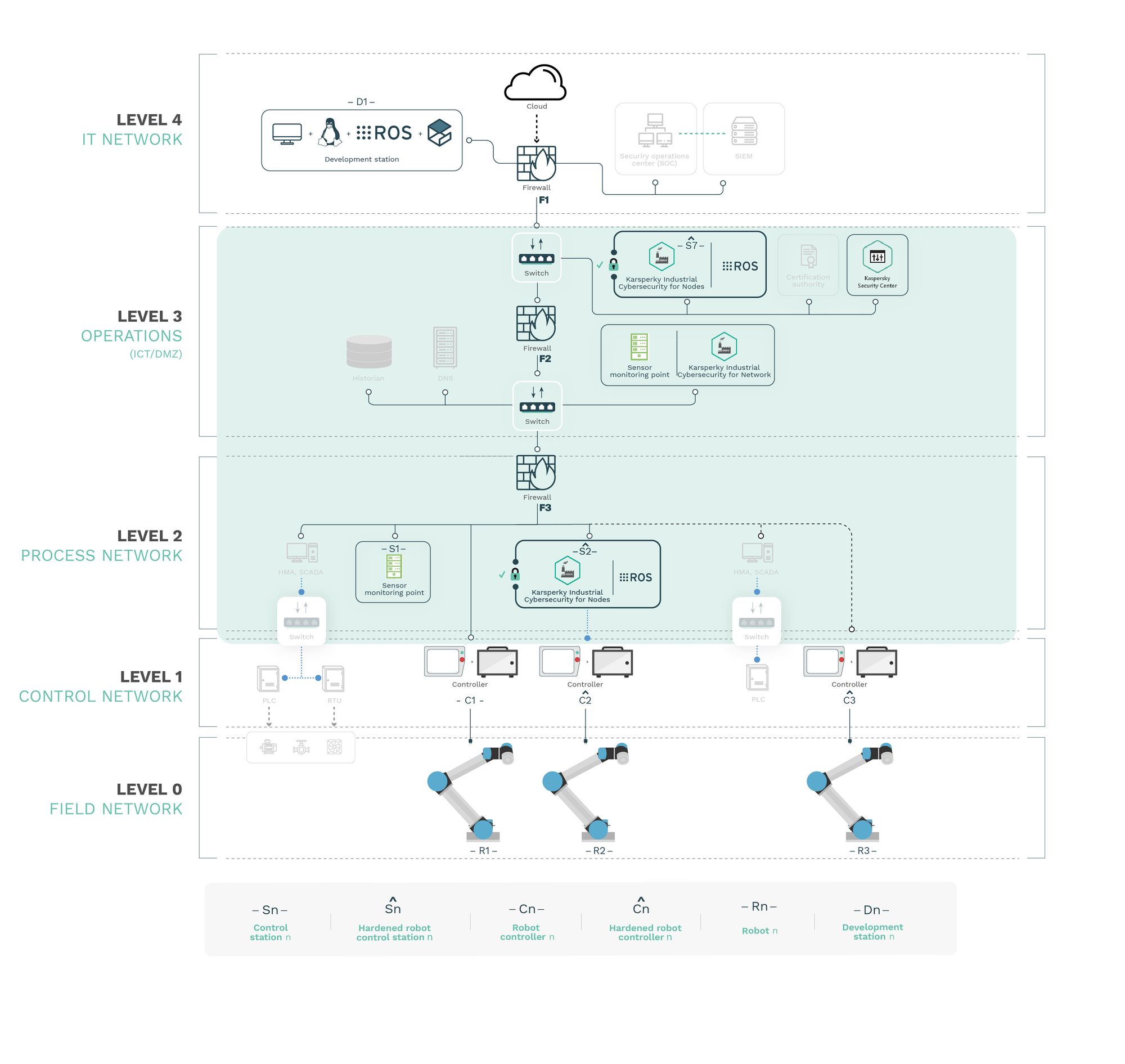
Attack vector 1: Process network insider
Attack vector 2: Controller insider
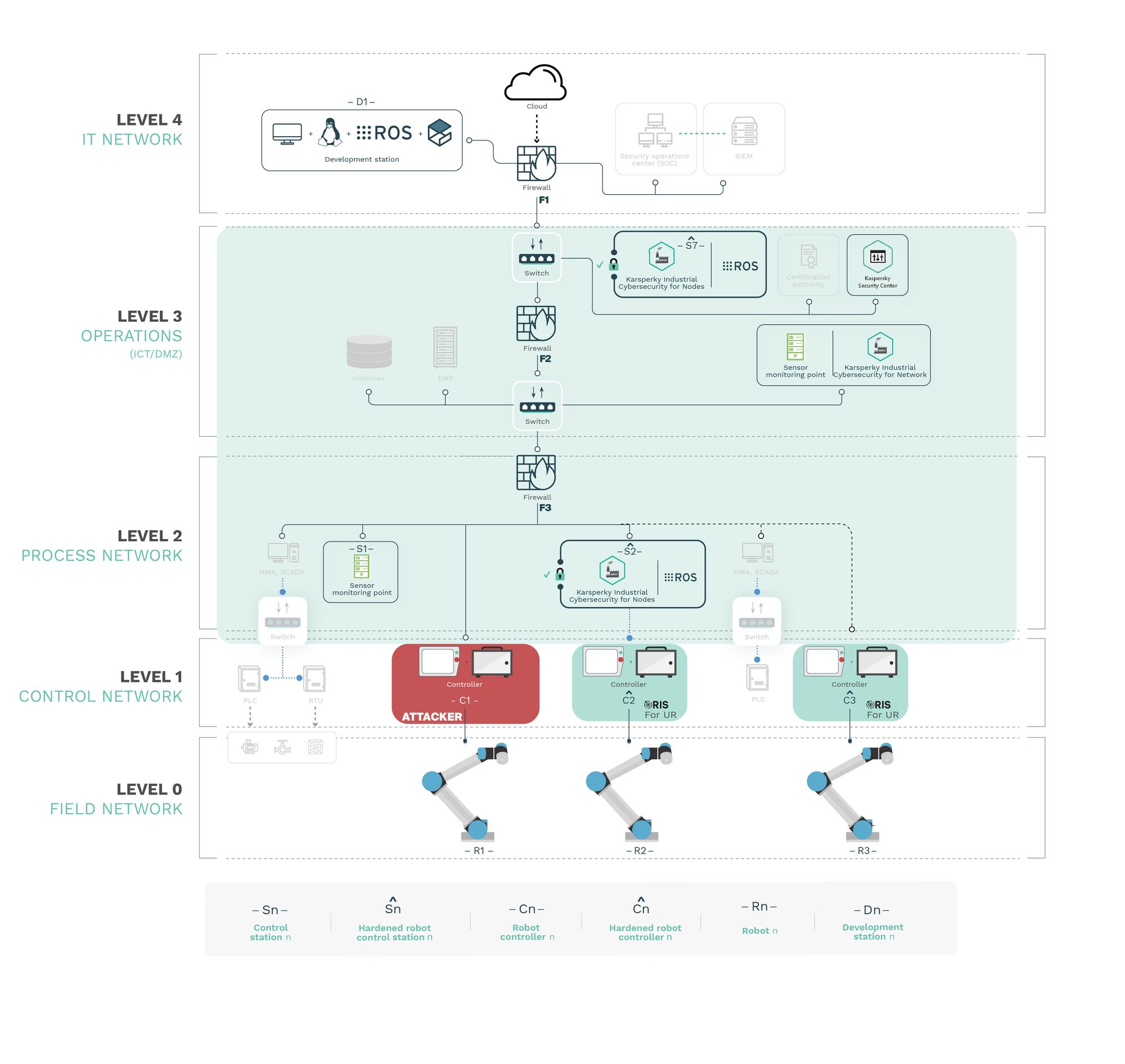
Attack vector 3: Compromising the ROS network
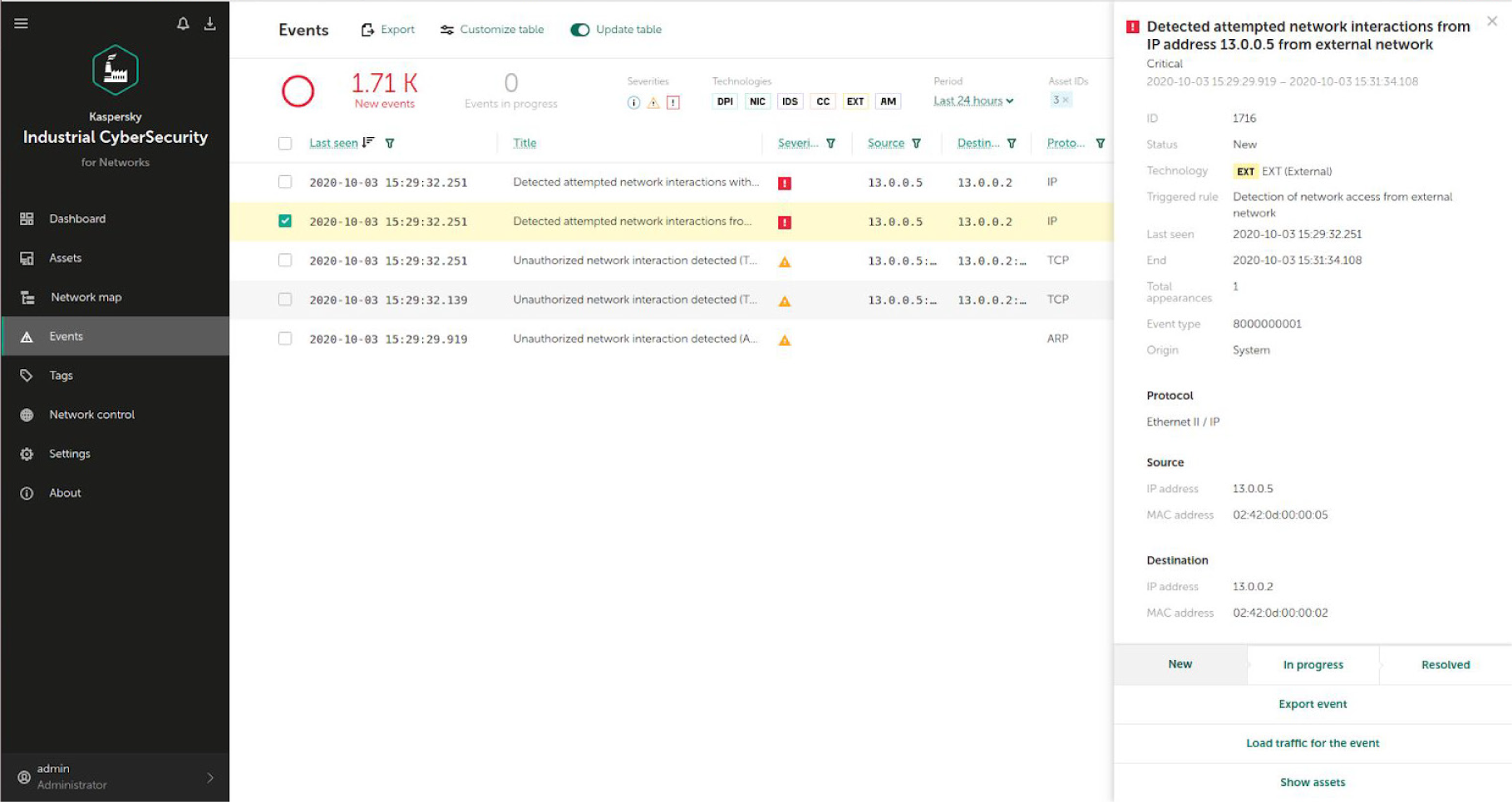
If you wish to learn more, read the complete case study here.
Conclusions
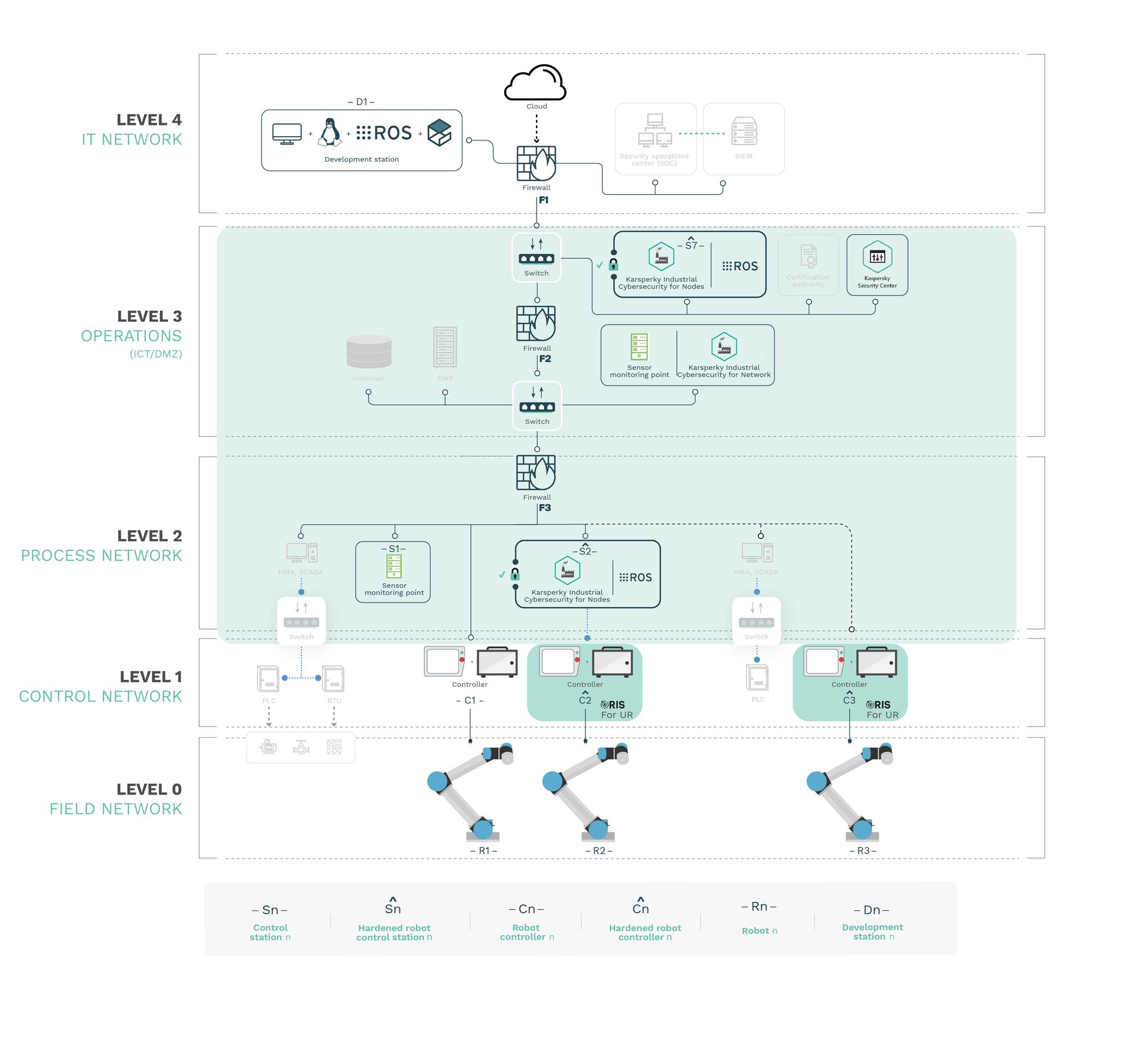
With RIS complementing KICS, robot controllers remained resilient to the same attacks, preventing any safety hazards
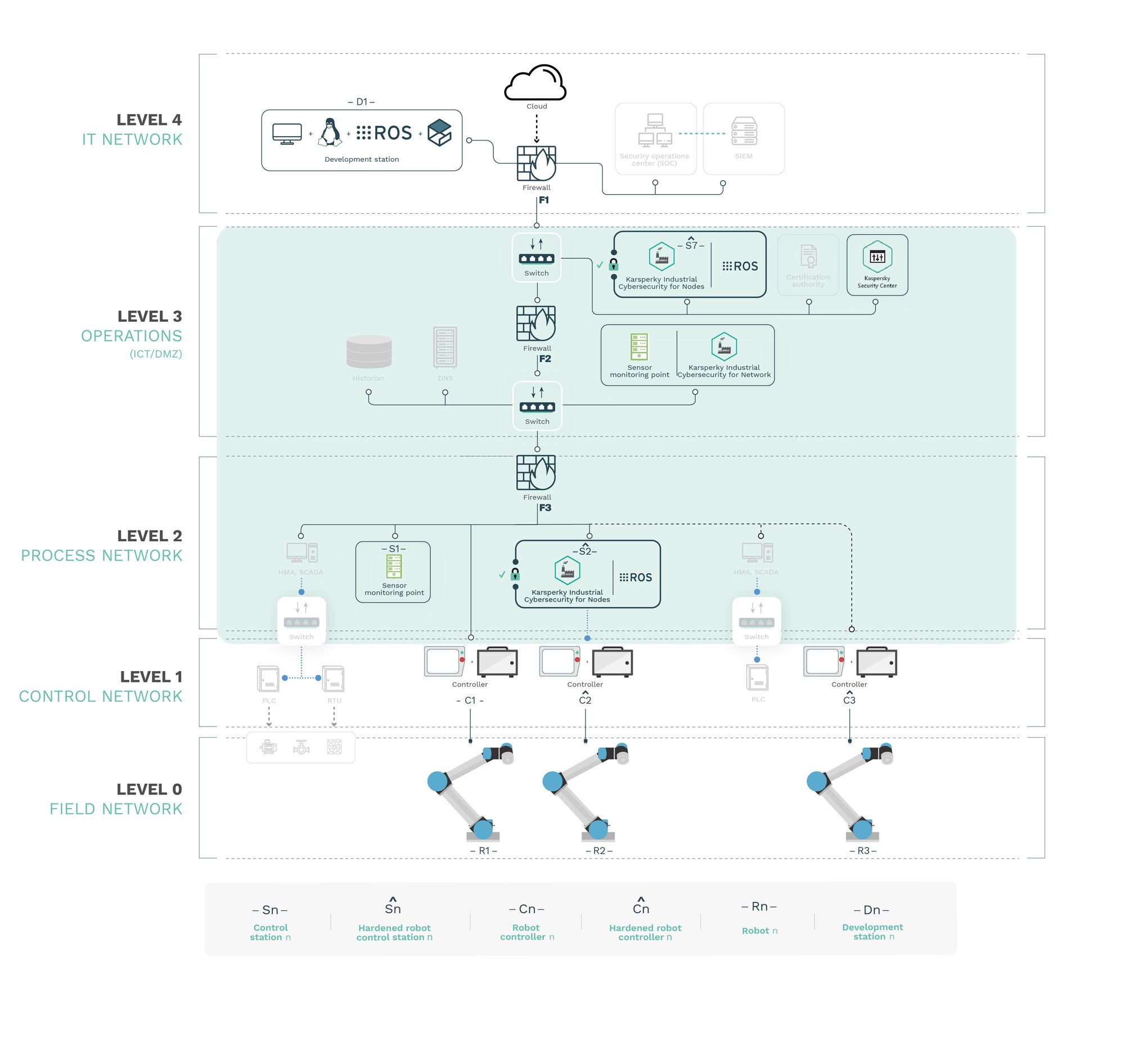
The results acquired through the research led Alias Robotics to conclude that the combination of the Robot Immune System (RIS, on each robot endpoint) together with the Kaspersky Industrial Cybersecurity (KICS) managed to jointly secure robot endpoints in OT environments.
KICS (and particularly KICS for Networks and Nodes) qualifies nicely as an industrial-grade solution to monitor environments with robotic endpoints; however beyond monitoring general industrial networks, additional security means must be used in combination with KICS to prevent robots from being compromised and cause safety hazards. Alias Robotics confirmed this with attacks targeting robot controllers and ROS networks. Alias Robotics also verified that the addition of RIS as a complementary solution successfully protects robot endpoints, mitigating the cybersecurity flaws of the selected robot endpoints and fulfilling the safety requirements.
From the research what is concluded is the following:
-
KICS for Networks successfully detects basic network attacks, even
those targeting robotic endpoints if the attack uses a channel sensed by
KICS. -
KICS for Nodes hardens control stations successfully and prevents them
from being affected by attacks. ROS can be embedded into such
hardened-stations. -
RIS enhancing KICS prevents attacks and protects robot endpoints.
-
RIS for UR protects the robot endpoints against targeted attacks and
can be used in combination with KICS for securing OT environments with
robot endpoints. -
The protection of ROS networks requires an extension of KICS for
Networks that grasp the complexity of the ROS API. RIS for ROS follows
such an approach and delivers an alternative protection for control
stations against targeted attacks.
L. Alzola Kirschgens, I. Zamalloa Ugarte, E. Gil Uriarte, A. Muñiz Rosas, and V.Mayoral Vilches, “Robot hazards: from safety to security,” ArXiv e-prints, Jun.2018. ↩︎
G. Lacava, A. Marotta, F. Martinelli, A. Saracino, A. La Marra, E. Gil-Uriarte, and V.M. Vilches, “Current research issues on cyber security in robotics,” 2020. ↩︎
J. McClean, C. Stull, C. Farrar, and D. Mascareñas, “A preliminary cyber-physical security assessment of the robot operating system (ros),” in Unmanned Systems Technolo-gy XV, vol. 8741. International Society for Optics and Photonics, 2013,
p. 874110. ↩︎G. Olalde Mendia, L. Usategui San Juan, X. Perez Bascaran, A. Bilbao Calvo, A. Hernández Cordero, I. Zamalloa Ugarte, A. Muñiz Rosas, D. Mayoral Vilches, U. Ayucar Car-bajo, L. Alzola Kirschgens, V. Mayoral Vilches, and E. Gil-Uriarte, “Robotics CTF (RCTF), a playground for robot hacking,” ArXiv e-prints, Oct. 2018. ↩︎
T. Olsson and A. L. Forsberg, “Iot offensive security penetration testing.” ↩︎
V. Mayoral-Vilches, L. U. S. Juan, U. A. Carbajo, R. Campo, X. S. de Cámara,
O. Urzelai, N. García, and E. Gil-Uriarte, “Industrial robot ransomware: Akerbeltz,” arXiv preprint arXiv:1912.07714, 2019. ↩︎S. Rivera, S. Lagraa, and R. State, “Rosploit: Cybersecurity tool for ros,” in the 2019 Third IEEE International Conference on Robotic Computing (IRC). IEEE, 2019, pp. 415–416. ↩︎
B. Dieber, R. White, S. Taurer, B. Breiling, G. Caiazza, H. Christensen, and A. Cortesi, “Penetration testing rros,” in Robot Operating System (ROS). Springer, 2020,
pp. 183–225. ↩︎ ↩︎M. Quigley, K. Conley, B. Gerkey, J. Faust, T. Foote, J. Leibs, R. Wheeler, and A. Y. Ng, “Ros: an open-source robot operating system,” in ICRA workshop on open source
sof-tware, vol. 3, no. 3.2. Kobe, Japan, 2009, p. 5. ↩︎F. Maggi and M. Pogliani, “Rogue automation: Vulnerabile and malicious code in industrial programming,” Trend Micro, Politecnico di Milano, Tech. Rep, 2020. ↩︎ ↩︎
Mayoral-Vilches, V., Abad-Fernández, I., Pinzger, M., Rass, S., Dieber, B., Cunha, A., ... & Gil-Uriarte, E. (2020). alurity, a toolbox for robot cybersecurity. arXiv preprint arXiv:2010.07759.
https://arxiv.org/pdf/2010.07759.pdf ↩︎ ↩︎ ↩︎


