From robot security researchers to manage robot vulnerabilities as a CNA - Alias Robotics talks about engagement with MITRE as a CVE Numbering Authority for robotics.
Alias Robotics is CNA since 2020. From then on, we have referenced more than 30 CVEs. Not only from our research but Third-parties robot-related vulnerabilities reports. We explain our procedure to get a CVE and why the conventional scoring method is not entirely valid for robot vulnerabilities.

According to the World Economic Forum, by 2025, the number of robots will be equal to human employees in the industry. This prediction opens up tons of possibilities, especially combining robotics and the latest connectivity technologies.
Alias Robotics' team always works to be a step forward. This is why we aim to make robots work securely close to humans. Last industrial robotics technologies have evolved faster than ever and cybersecurity has not been at the core. The advent of IoT, industry 4.0, and its connectivity changed the game forever. Day by day robot security is becoming more relevant, especially knowing that the more connectivity in robotics and industry, the greater the risk to be vulnerable to bad-intentioned attacks.
Our engineers, specialists in robotics and cybersecurity, research security vulnerabilities. Then, our endpoint protection platform RIS (Robot Immune System) mitigate them. With the security research, we also look for robot users’ empowerment, so they are aware of the security issues of their robotic platforms.
Due to our research and the company's motivation, Alias Robotics became a CVE Numbering Authority (CNA) in February 2020. Since then, more than 30 CVEs IDs have been issued and referenced. All of them affect robots or robotic components. Apart from CVE IDs, Alias Robotics is continuously looking for robot security vulnerabilities in client-related projects. This is why most of our work has to remain private within the confidentiality we owe to our clients.
As a CNA, many researchers report vulnerabilities to Alias. In case there is a novel robot vulnerability, we differentiate between our discoveries and those reported to us by researchers. When our team finds a vulnerability on a non-confidential project, we immediately report it (via a secure channel) to the robot manufacturer, so they can fix it. When the manufacturer responds and acknowledges it, we typically make it public after 90 days in RVD, aiming full transparency at the security process and also incentivizing prompt fixing of issues. Sadly, this is not always the case.
We have an email for those security researchers who wish to send us their findings. When a third-party sends a vulnerability, our technicians ask for a temporary CVE ID until we triage it. Once they have checked the report and ensured its reliability, and reproducibility, they finally award the vulnerability a CVE ID.
After many cybersecurity investigations, Alias Robotics concluded that classic scoring methods, such as the Common Vulnerability Scoring System (CVSS), are not able to accurately capture the severity of robot vulnerabilities. Therefore, the Alias Robotics team worked on the creation of an open and free access Robot Vulnerability Scoring System (RVSS) that considers major relevant issues in robotics.
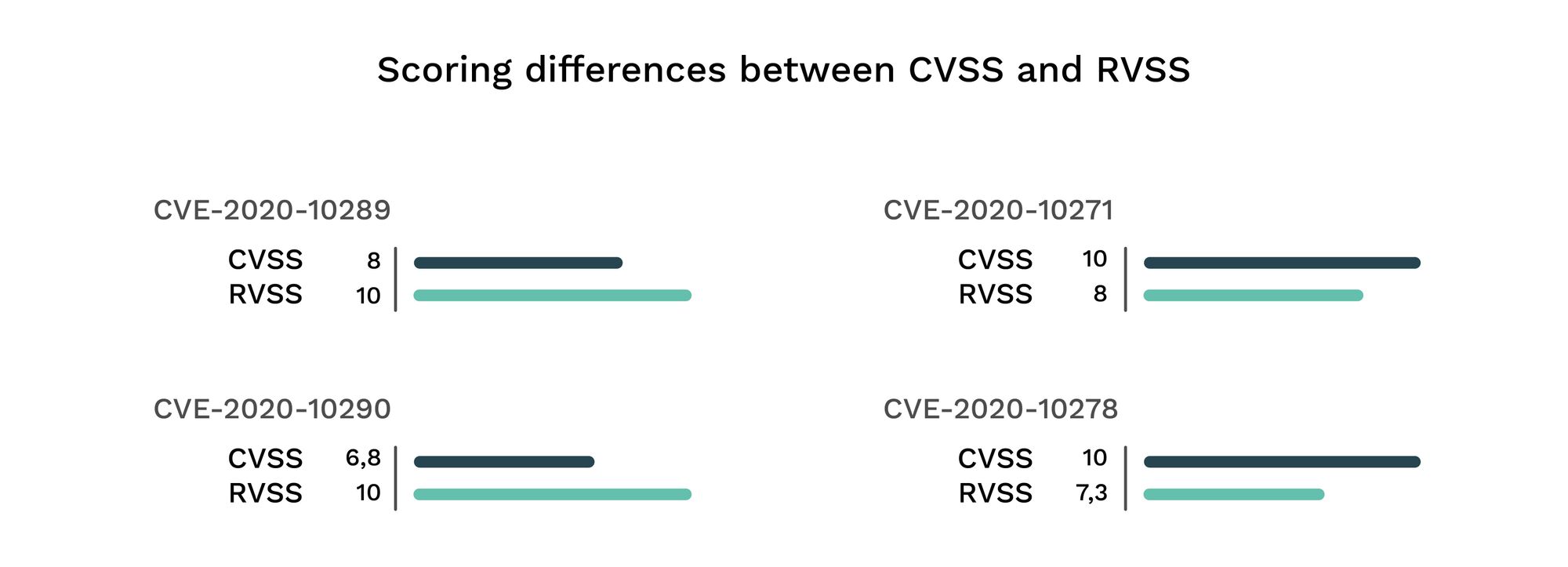
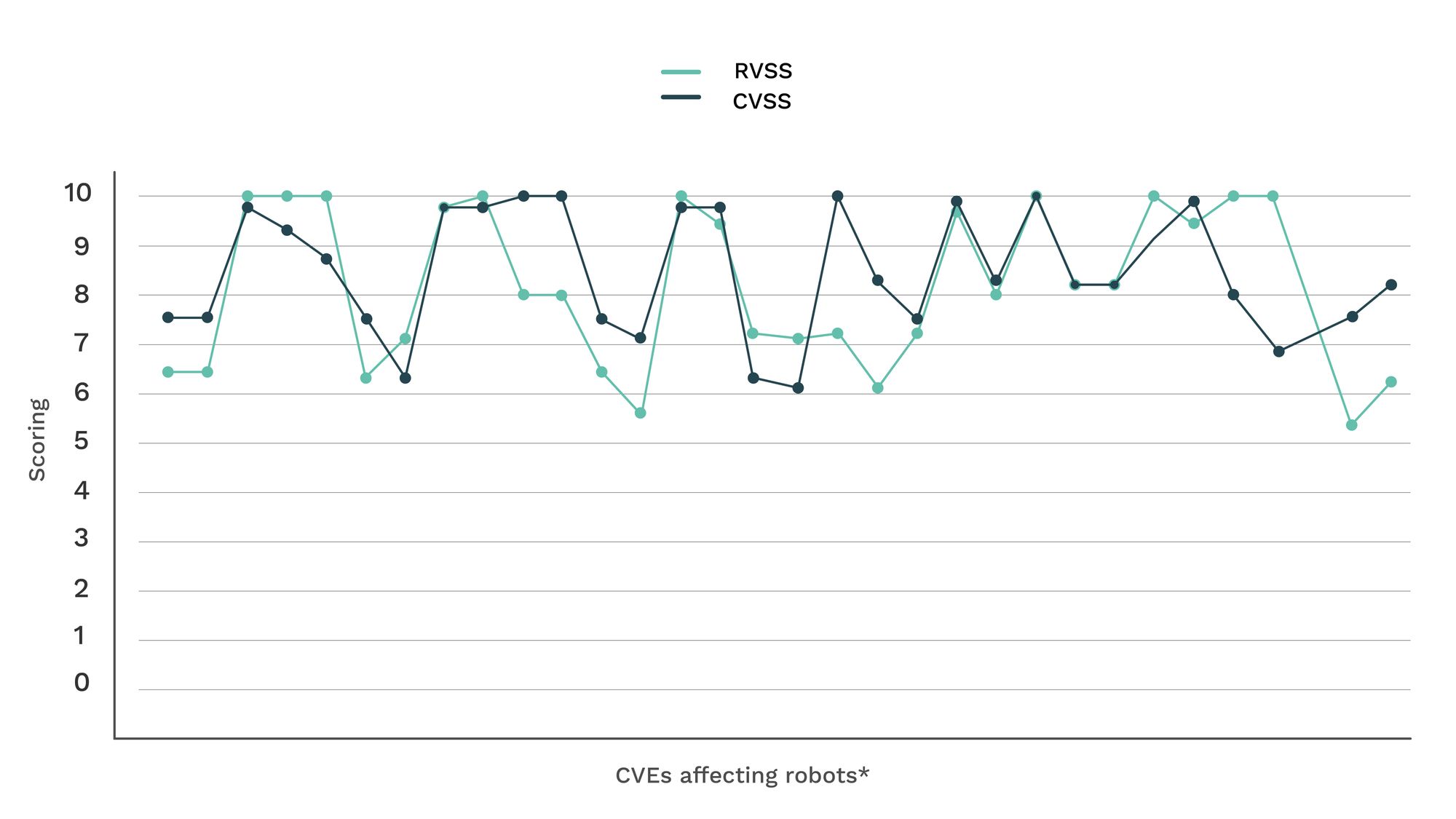
Being a CNA is a way to show Alias Robotics' commitment to the cybersecurity community and industrial robot users. Vulnerability disclousure, via official channels, like MITRE, officialize and adds value to secury research. Certifying vulnerabilities is how we enhance Robot cybersecurity research and securitization.
*CVEs affecting robots
CVE-2019-19625 https://github.com/aliasrobotics/RVD/issues/922
CVE-2019-19626 https://github.com/aliasrobotics/RVD/issues/1408
CVE-2019-19627 https://github.com/aliasrobotics/RVD/issues/926
CVE-2020-10264 https://github.com/aliasrobotics/RVD/issues/1444
CVE-2020-10265 https://github.com/aliasrobotics/RVD/issues/1443
CVE-2020-10266 https://github.com/aliasrobotics/RVD/issues/1487
CVE-2020-10267 https://github.com/aliasrobotics/RVD/issues/1489
CVE-2020-10268 https://github.com/aliasrobotics/RVD/issues/2550
CVE-2020-10269 https://github.com/aliasrobotics/RVD/issues/2566
CVE-2020-10270 https://github.com/aliasrobotics/RVD/issues/2557
CVE-2020-10271 https://github.com/aliasrobotics/RVD/issues/2555
CVE-2020-10272 https://github.com/aliasrobotics/RVD/issues/2554
CVE-2020-10273 https://github.com/aliasrobotics/RVD/issues/2560
CVE-2020-10274 https://github.com/aliasrobotics/RVD/issues/2556
CVE-2020-10275 https://github.com/aliasrobotics/RVD/issues/2565
CVE-2020-10276 https://github.com/aliasrobotics/RVD/issues/2558
CVE-2020-10277 https://github.com/aliasrobotics/RVD/issues/2562
CVE-2020-10278 https://github.com/aliasrobotics/RVD/issues/2561
CVE-2020-10279 https://github.com/aliasrobotics/RVD/issues/2569
CVE-2020-10280 https://github.com/aliasrobotics/RVD/issues/2568
CVE-2020-10281 https://github.com/aliasrobotics/RVD/issues/3315
CVE-2020-10282 https://github.com/aliasrobotics/RVD/issues/3316
CVE-2020-10283 https://github.com/aliasrobotics/RVD/issues/3317
CVE-2020-10284 https://github.com/aliasrobotics/RVD/issues/3321
CVE-2020-10285 https://github.com/aliasrobotics/RVD/issues/3322
CVE-2020-10286 https://github.com/aliasrobotics/RVD/issues/3323
CVE-2020-10287 https://github.com/aliasrobotics/RVD/issues/3326
CVE-2020-10288 https://github.com/aliasrobotics/RVD/issues/3327
CVE-2020-10289 https://github.com/aliasrobotics/RVD/issues/2401
CVE-2020-10290 https://github.com/aliasrobotics/RVD/issues/1495
CVE-2020-10291 https://github.com/aliasrobotics/RVD/issues/3336
CVE-2020-10292 https://github.com/aliasrobotics/RVD/issues/3337


